Install Wireguard on Docker
You will need to have Docker and Docker-compose before you can do this part. This is the .yaml file that needs to be configured.
.yml
version: "2.1"
services:
wireguard:
image: lscr.io/linuxserver/wireguard:latest
container_name: wireguard
cap_add:
- NET_ADMIN
- SYS_MODULE #optional
environment:
- PUID=1000
- PGID=1000
- TZ=Etc/UTC
- SERVERURL=wireguard.domain.com #optional
- SERVERPORT=5000 #optional (make sure this is the same as the below external-host port in "ports:")
- PEERS=peer1,guest1 #optional
- PEERDNS=auto #optional
- INTERNAL_SUBNET=10.13.13.0 #optional
- ALLOWEDIPS=0.0.0.0/0 #optional
- PERSISTENTKEEPALIVE_PEERS= #optional
- LOG_CONFS=true #optional
volumes:
- /path/to/appdata/config:/config
- /lib/modules:/lib/modules #optional
ports:
- 5000:51820/udp #external-host_port:docker_port/udp
sysctls:
- net.ipv4.conf.all.src_valid_mark=1
restart: unless-stoppedYou will need open your port (port forwarding) on port 5000 in order for this to work. Make sure that "SERVERPORT" and the host port specified match. In this case, 5000 was used.
I have didn't want to expose another port so I used replaced 5000 with port 80. So far, I have had it clash with anything else on my server using port 80. Give it a shot. see what happens.
Run the container:
sudo docker-compose up -dUp and running? GOOD!
Now lets go find the files we need get create that tunnel from the client, to this VPN server.
In your docker-compose.yml file, you created a path to the config file (i hope). To into that config file and find file called peer_peer1. You can customize that name if you want.
In the config file, if you put "PEERS=bob" That file name would have been, "peer_bob" but, in this case, we called it "peer1. Make as many as you like.
Once you are inside that file. Mine is named "guest1 so, i went into that file.
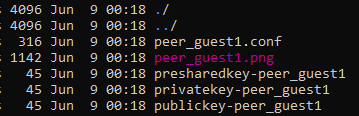
/path/to/appdata/config/peer_peer1Notice the files that are there. The name of your peer is what you want. so, peer_guest1.conf and .png
The .png is a QR code that you can use on a mobile app and the .conf has the info needed when connecting to a computer.
If you cant use the machine you have this file stored, transfer one or both of those (securely) to another machine that can open the QR code so that you can use the app. or,
on a computer, in the app, you will transfer that .conf file in the computers app.
Now on the client, the phone or computer you want to create a tunnel to connect to your VPN server, download the wireguard app and use the QR code or .conf.
uh... you should be in. check your ip. is it working? I hope so. Have fun.
No Comments